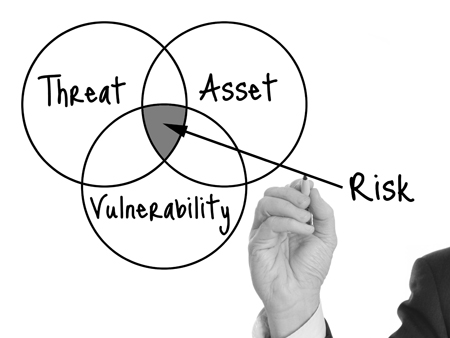
As part of the overall Disaster Recovery (DR) and Business Continuity Plan (BCP), organizations must look into certain time sensitive factors hence put into practice a thorough business impact analysis. When implemented properly, this all contributes to the overall success of an organizations’ Cyber Security strategy.

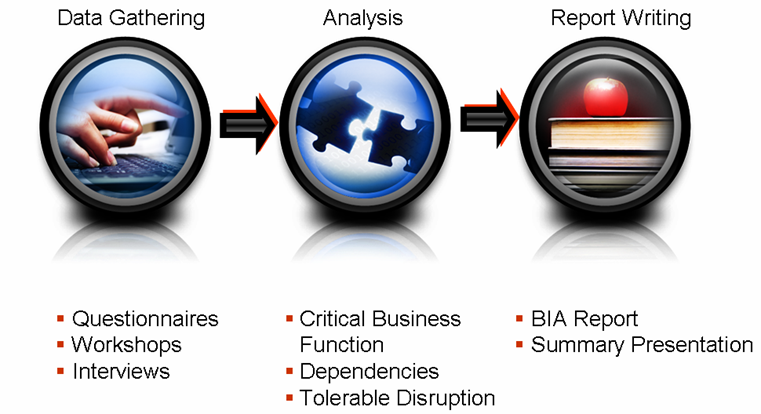
As discussed previously, Business Impact Analysis helps a company decide exactly what needs to be recovered and in what amount of time. There are 2 different types of analysis that business planners take into consideration:
Quantitative Decision Making: Basically, this involves the use of numbers and formulas to make a decision. As a result, the data often expressed is in terms of dollar value for the business.
Qualitative Decision Making: This type of decision making take into account non-numerical factors such as emotions, investor/customer confidence and stability among other concerns.
The Cyber Security team incharge of BCP needs to assess all the organizations’ assets and then assign an asset value (AV) in monetary terms to each asset. The second quantitative measure that team must look into is the maximum tolerable downtime (MTD) also known as maximum tolerable outage (MTO). In a nutshell, the MTD is the maximum length of time an organization function can be inoperable without causing irreparable harm to the business. Overall, MTD provides crucial information and when an organization is performing both BCP and DR planning. The Recovery Time Objective (RTO) should also be considered for each organization function. This is basically, the amount of time in which you think the organization can easily function in the event of disruption. Furthermore, Recovery Point Objective (RPO) also needs to taken into account which basically tells the planner the point of time up until the data needs to be recovered.
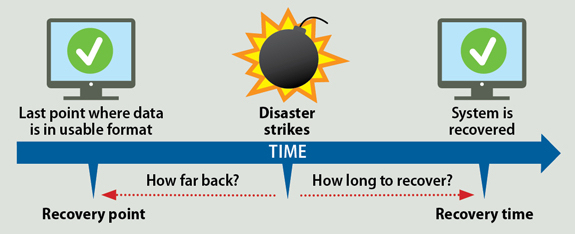
Overall, the goal of BCP process is to ensure that businesses RTO are less than their MTDs resulting in situation in which a business function should never be unavailable beyond the maximum tolerable downtime. The man made and natural risks also need to be identified as well. Besides the loss in terms of monetary amount other qualitative points of view need to be considered such as:
1.) Loss of trust among your client base
2.) Loss of employee to other jobs after lengthy downtime
3.) Social and Ethical responsibilities to the community
4.) Getting negative publicity
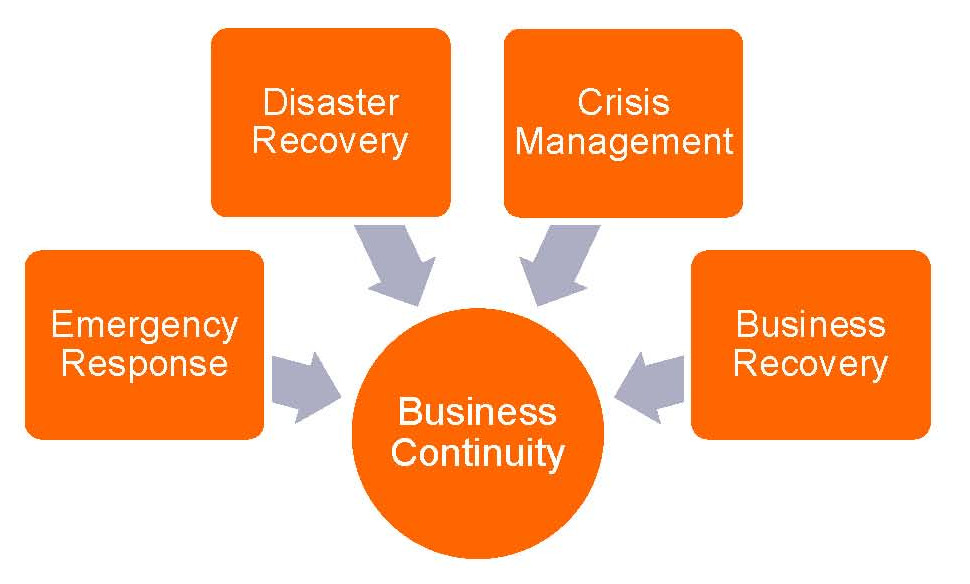
In conclusion, BIA can prove invaluable to the overall success of the organization. As result, this can save organization thousands and even millions of dollars when done properly. The security consultants at Silex Systems can guide an organization to meet their BIA and cyber security needs.






 Let the truth be told. Disasters are bound to happen whether they are in the form of tornadoes, hurricanes, earth quake, floods or even fire. In other words, organizations worldwide need to have plan in place to deal with potential natural or human-induced disasters. By following a few guidelines, organizations of any size can be well prepared before disaster strikes.
Let the truth be told. Disasters are bound to happen whether they are in the form of tornadoes, hurricanes, earth quake, floods or even fire. In other words, organizations worldwide need to have plan in place to deal with potential natural or human-induced disasters. By following a few guidelines, organizations of any size can be well prepared before disaster strikes.